Let’s start with the basics, a summary of what is in this post:
- How to enable DNS in ZeroTier, and what it gets you…
- ZeroNSD — the flagship DNS implementation for ZeroTier — version 0.4.2 is out, with tons of new features, which we’ll talk about below. We’ll cover the differences from the 0.1 series forward.
- zerotier-systemd-manager is here to make your lives easier on Linux with split-horizon DNS, which ZeroTier needs to behave like an adult on your device. We’ll cover setup and how it works under the hood.
- If you don’t have or can’t use systemd, you’re good if you’re on OS X or Windows. Otherwise, you may want to consider the polyresolver project which works a lot like systemd-resolved. We’ll cover setup of polyresolver in those situations.
- Finally, some thanks to the community who has made this possible, notably Benjamin Fry and the trust-dns team, what most of this work is based on. And rust, of course. 🙂
But most importantly, I’d like to thank the rest of the team at ZeroTier for being so generous with time allocation and understanding as this project has matured. Proper DNS support has been nearly a year in the making at ZeroTier at this point, and without that, it probably would have failed miserably.
Why DNS?
So some of you who have been using ZeroTier for a while may be wondering “why bother with DNS?”. This part isn’t for the rest of you. 🙂
Notably, DNS enables portable names for your addresses. While ZeroTier has the notion of identities that are independent from IP addresses, the IP stack must still be traversed for you to reach your host, and that means using an address. ZeroNSD enables floating and re-assignable IP addresses within 30 seconds or less from IP change, so if you do need to change things, you won’t break everyone.
Additionally, TLS certs are extremely dependent on DNS, something that will become more and more crucial in a world full of security issues — ones that ZeroTier is designed to prevent, but alas, cannot mitigate completely by itself.
How to enable DNS in ZeroTier
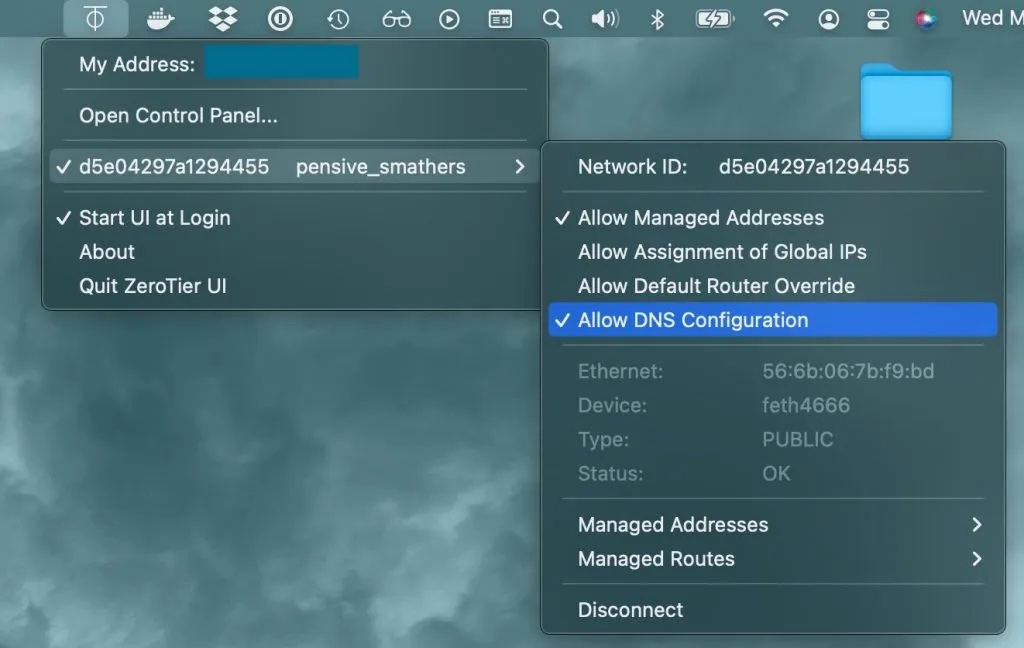
For GUI users, the solution is as simple as checking the “Allow DNS” flag in ZeroTier’s GUI.
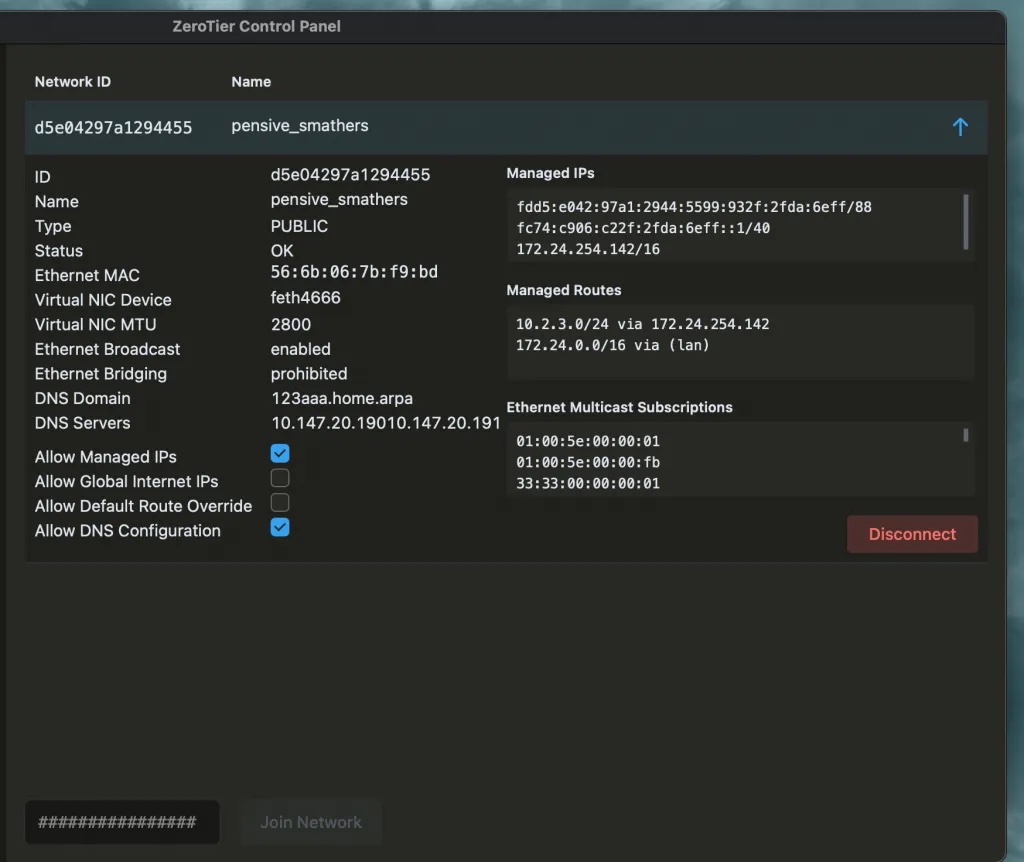
For OS X and Windows CLI users, you must set the allowDNS flag to true in the CLI.
$ zerotier-cli set allowDNS=true
If you see a bunch of JSON output, you’ve done the right thing.
You must rejoin your network for changes to take effect (leave then join).
For Linux users, we provide zerotier-systemd-manager which just needs to be installed to work in most instances. See how to do more with it in further sections below.
Serving DNS over ZeroTier
Fundamentally, ZeroTier just provides an IP and you can run any DNS server against it by listening on its IP address(es). Nothing is keeping you from running BIND9 or Unbound against a ZeroTier network.
However, this way you’re stuck editing DNS names in one spot and configuring ZeroTier IP infrastructure at another. ZeroNSD syncs your ZeroTier node names in ZeroTier Central as DNS names in the service so they can be resolved by your DNS resolver. This allows for a one-stop place to edit all the infrastructure on your ZeroTier network. ZeroNSD relies on the trust-dns framework of libraries to provide DNS instead of rolling its own implementation, allowing for maximum robustness when it comes to your DNS needs.
What’s happened to ZeroNSD since 0.1.0?
Our last blog post on ZeroNSD was posted almost a year ago, promoting it in alpha. A lot has happened since then!
- PTR record support for IPv6.
- Easier methods of supervision (zeronsd supervise); supports systemd and OS X.
- Better docker support.
- Good support for Alpine, Windows, and Homebrew (OS X).
- RFC4193 & 6Plane support.
- Wildcard domains support.
- Robust Logging with levels.
- Robust Testing Framework.
- Name coercion: if you have a non-DNS name in the names field in Central, it’ll be transformed into a DNS name (like Mac OS).
- Can be embedded as a rust library.
- Multiple Listening Addresses if the ZeroTier instances is assigned more than one.
- IPv6 listener support.
- Firewall Punching for Windows (installer-only).
- Better support for forwarding records to an upstream DNS provider in situations where the TLD does not match.
- Configuration files instead of just CLI arguments.
- Using the DNS-standard home.arpa. as the default domain.
- DNS-over-TLS support!
We use it internally, I use it at home for my family to make life easier for them to get at zerotier-enabled services I run in the home. We have many other users contributing to the project through bug reports and patches. If you were on the fence about its stability, you should give it a shot.
Getting AllowDNS on Linux – zerotier-systemd-manager
If you’re a Linux user, you may have noticed that the allowDNS flag doesn’t do much on it. This is because Linux doesn’t have a canonical way of doing split-horizon DNS, or the notion that some domains will direct to some nameservers, and other domains to other nameservers. zerotier-systemd-manager enables this by injecting a small systemd timer that runs a program that populates /etc/systemd/network.d with configuration that points your ZeroTier configured domains to the DNS server of choice.
Note, that you do not need to use ZeroNSD to leverage zerotier-systemd-manager, just a DNS server that’s populated in the ZeroTier Central UI.
Don’t have systemd, OS X, or Windows?
If you don’t have systemd, OS X, or Windows, you have two (major) options for split-horizon DNS at the client:
- You can direct everything at ZeroNSD — it will act as a backup forwarding plane for your root-level DNS server in a pinch.
- Try the polyresolver project, a new project to provide systemd-resolved functionality without systemd. Just point /etc/resolv.conf at it and add configuration files to a directory as your system brings interfaces up.
Some final words
Thanks to all of those who made this project possible. There are a lot of people to thank and I did most of that at the top, so I’ll spare you a repeat.
We plan to do a lot more with ZeroNSD, particularly over the next few months and we’re going to be looking for help, so if this sounds like something you’re interested in, reach out directly or at the repository.

